How important is secure identity management to you? If you’re like most, it is a top priority. In today’s post I’ll talk about Azure Active Directory B2C which is an identity management service that enables you to customize and control how users securely interact with your web, desktop, mobile or even single applications.
Using Azure AD B2C, users can sign up, sign in, reset passwords and edit profiles for the various applications they’re using. When implementing these policies, we’ll have two choices:
- Using common identity user flows within the Azure portal or,
- For the more skilled developer or if the templates in the portal don’t support your use case, you can use XML based custom policies.
Once you make that decision, your choice will define the path of authentication, commonly referred to as the user journey. User journeys allow you to control behaviors by configuring some settings; things like social accounts (like Facebook) that the user uses to sign up for the application.
Data collected from the user as a first name or postal code would be used for authentication. You also have multi-factor authentication options, as well as the look and feel of how users interact with pages and information returned to the application.
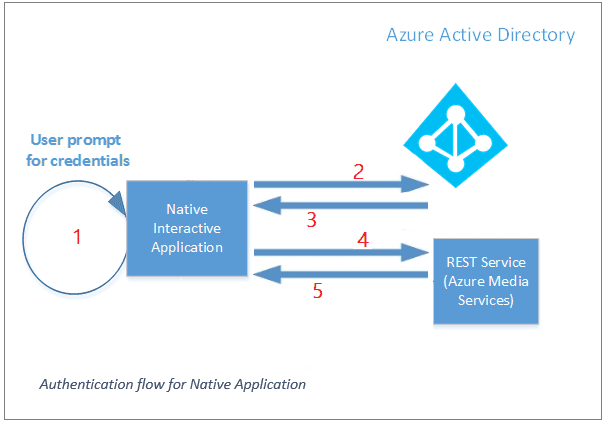
Azure Active Directory B2C supports the open ID connect and the OAuth 2 protocols for these user journeys. These protocols will help ultimately receive a token that will allow for you to be authenticated. The interaction of every application follows a similar high-level pattern shown in the graphic below:
The steps here are:
1. The application directs the user to run a policy.
2. The user completes the policy according to the policy definition.
3. Then the application receives a token.
4. And then uses that token to try to a resource.
5. The resource server then validates the token to verify that access can be granted.
6. And the application will periodically refresh in the background ( there really are 5 steps but this 6th step is happening over and over).
Azure AD B2C can also work with additional identity providers such as Amazon, Facebook and Google that will create, maintain and manage identity information while providing authentication services to their (and other) applications.
Typically, you would only use one identity provider in your application but there are no restrictions for using more if your use case calls for it.
The main value for this service is the ability to lessen the need for username and password management for so many applications, thus improving the user experience. Our lives have been made a bit easier since we now have many applications, both web and desktop based, that allow that single sign on or no sign on experience because they are already pre-authenticated with a service like this.
Need further help? Our expert team and solution offerings can help your business with any Azure product or service, including Managed Services offerings. Contact us at 888-8AZURE or [email protected]<